Whitelist Simulations in Exchange Online
This guide describes how to allowlist Nimblr's Simulated Attacks in Microsoft Exchange Online.
Whitelist Connection Filter
1. Start with opening the Anti-Spam settings in the Microsoft Defender 365 portal at https://security.microsoft.com/antispam
2. Click Connection filter policy (Default) and then click Edit policy connection filter policy (click the text “Edit policy connection filter policy” - not its checkbox).
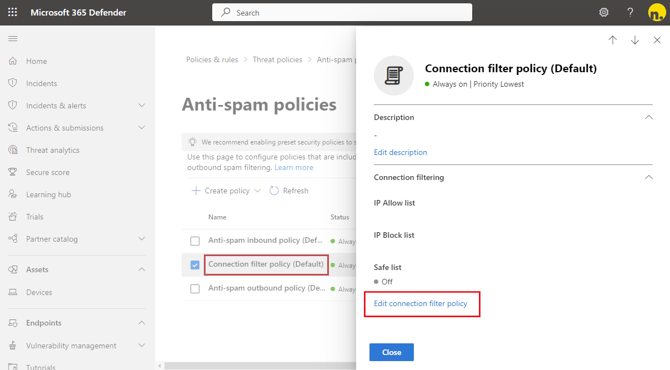
3. Add the following IP addresses one at a time and click Enter (so that they appear in gray boxes like in the picture bellow) and then click Save and Close
- 78.47.225.98
- 116.203.167.208
- 95.216.176.28
If you are using Antivirus, Spamfilter or other scanning tools outside of Microsoft:
If your organization uses external spamfilters, scanning tools or if messages are filtered so the domain's MX record does not point to Office 365, then this could lead to having clicks on simulations registered even when the user has not interacted with the email. Leading to the statistics and data being unreliable.
Please be sure to verify and configure in all systems that interact with the mail flow, inboxes or links being received by the organization.
If you'd like to add extra safety to get around this potential issue then you'll need to enable Enhanced Filtering for Connectors (also known as skip listing).
For more information, see Manage mail flow using a third-party cloud service with Exchange Online.
If you don't want Enhanced Filtering for Connectors, use mail flow rules (also known as transport rules) to bypass Microsoft filtering for messages that have already been evaluated by third-party filtering.
For more information, see Use mail flow rules to set the SCL to -1 in messages.
For whitelisting in any other tool you have you can use the same IP's, Domains & URL's as in the guide below.
For bypassing a spamfilter where you can't whitelist correctly, we can try sending directly to your organizations MX host.
To do this, please Submit a Ticket to our support team with your Exchange Host name included, see how to here: Find your Exchange Hostname
Microsoft Advanced Delivery Policy
To keep your organization secure by default, Exchange Online Protection (EOP) does not allow safe lists or filtering bypass for messages that are identified as “high confidence phishing”. To override this, the Advanced Delivery policy must be configured to allow delivery of third-party phishing simulations to users.
1. Go to the Microsoft 365 Defender Advanced delivery page: https://security.microsoft.com/advanceddelivery
2. Click Phishing Simulations and then click Add
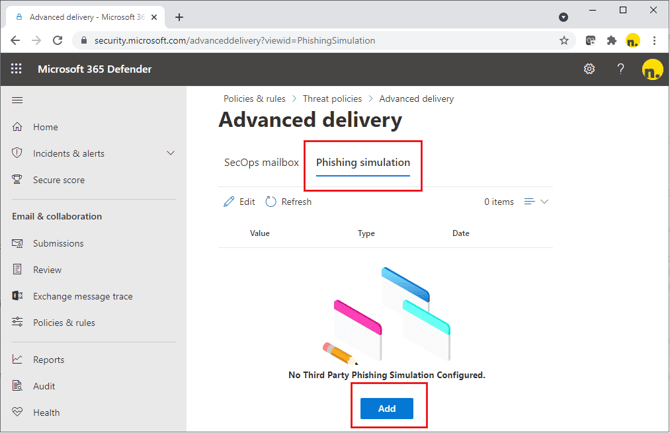
3. On the Third-party phishing simulation flyout that opens, configure the following settings:
- Sending domain: nimblr.net, sasender.net and awrns.net
- Sending IP: 78.47.225.98, 116.203.167.208, 95.216.176.28
- Simulation URLs to allow: 135461223.site/*, 953611493.site/*, 1491321218.site/*, nimblr.net/* and awrns.net/*

When you're finished, click Save. The Nimblr phishing simulation entries that you configured are now displayed on the Phishing simulation tab. Click Close.
To avoid the built-in warning notifications in Outlook or DMARC issues when using internal email domains for Ghost Senders you may consider to Allow Nimblr's Spoofed Senders
Allow Nimblr's Spoofed Senders in Exchange Online
To avoid the built-in warning notifications in Outlook or DMARC issues when using internal email domains for Ghost Senders you may consider configuring the Tenant Allow list for Spoofed Senders.
The warning message:
"We could not verify the identity of the sender. Click here to learn more."
This will be shown in most Outlook clients if you are not allowing spoofed senders, follow the steps below to configure the Allow Tenant list for spoofed senders in the Nimblr simulations and hide the warning notification in Outlook.
- Go to the Microsoft 365 Defender Policies & rules > Threat policies page: https://security.microsoft.com/threatpolicy

- Click Tenant Allow/Block List, select the Spoofed Senders tab, and click Add

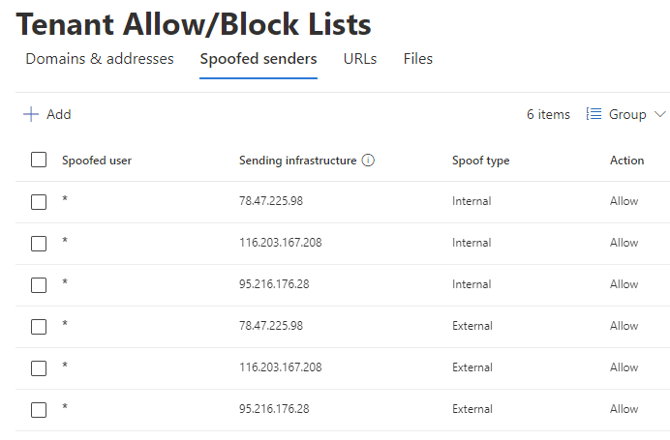
- Copy and paste all of the following data (including the star characters) into the box:
*, 78.47.225.98
*, 116.203.167.208
*, 95.216.176.28 - Select “Spoof type” to Internal and set “Action” to Allow, then click Add.
Then;
Select “Spoof type” to External and set “Action” to Allow, then click Add.
There should now be 6 entries in the Tenant Allow/Block Lists.
Banners and disclaimers:
If you are utilizing additional functionalities such as mail flow rules or third-party software to append disclaimers or banners to external emails, you may need to create exceptions for Nimblr simulations. This will help prevent these simulations from being marked as external or receiving warning notifications.
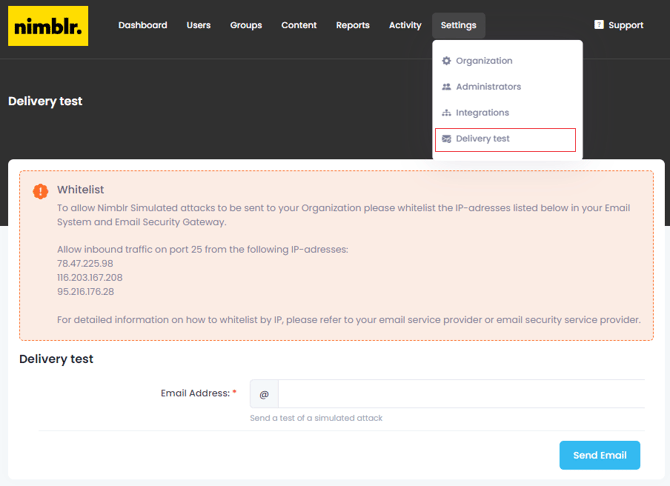
Verify Whitelist Configuration
Send a test simulation to verify that your whitelist configurations are functional. Login to your Nimblr portal on https://nimblr.net and navigate to Settings > Delivery test. Send a test simulation to a by clicking Send Email.